Setting up a secure and scalable cloud environment is one of the first challenges organisations face when adopting AWS. A landing zone provides a good foundation for cloud adoption, ensuring security, governance, and scalability from day one.
There are multiple ways to build a landing zone. Some organisations design their own custom environment from scratch, while others leverage AWS Control Tower, which offers an automated, best-practice implementation. While custom setups allow for flexibility, Control Tower is the best choice for most organisations because it simplifies deployment, enforces security policies, and provides a structured and scalable way to manage multiple AWS accounts.
Landing zones can range from simple setups to highly complex architectures, depending on an organisation’s needs. Two examples are illustrated below.
A more elaborate landing zone could also be created, perhaps geared towards a generally larger-scale environment, or one focused on a certain domain or solution set. As an example, a hybrid cloud landing zone would extend the basic landing zone by including additional network-related elements.
Basic Landing Zone
A basic, bare-bones landing zone can be created by selecting the most minimal options during the Control Tower configuration. This would still include essential security and governance, and provide a structured way to manage AWS accounts.
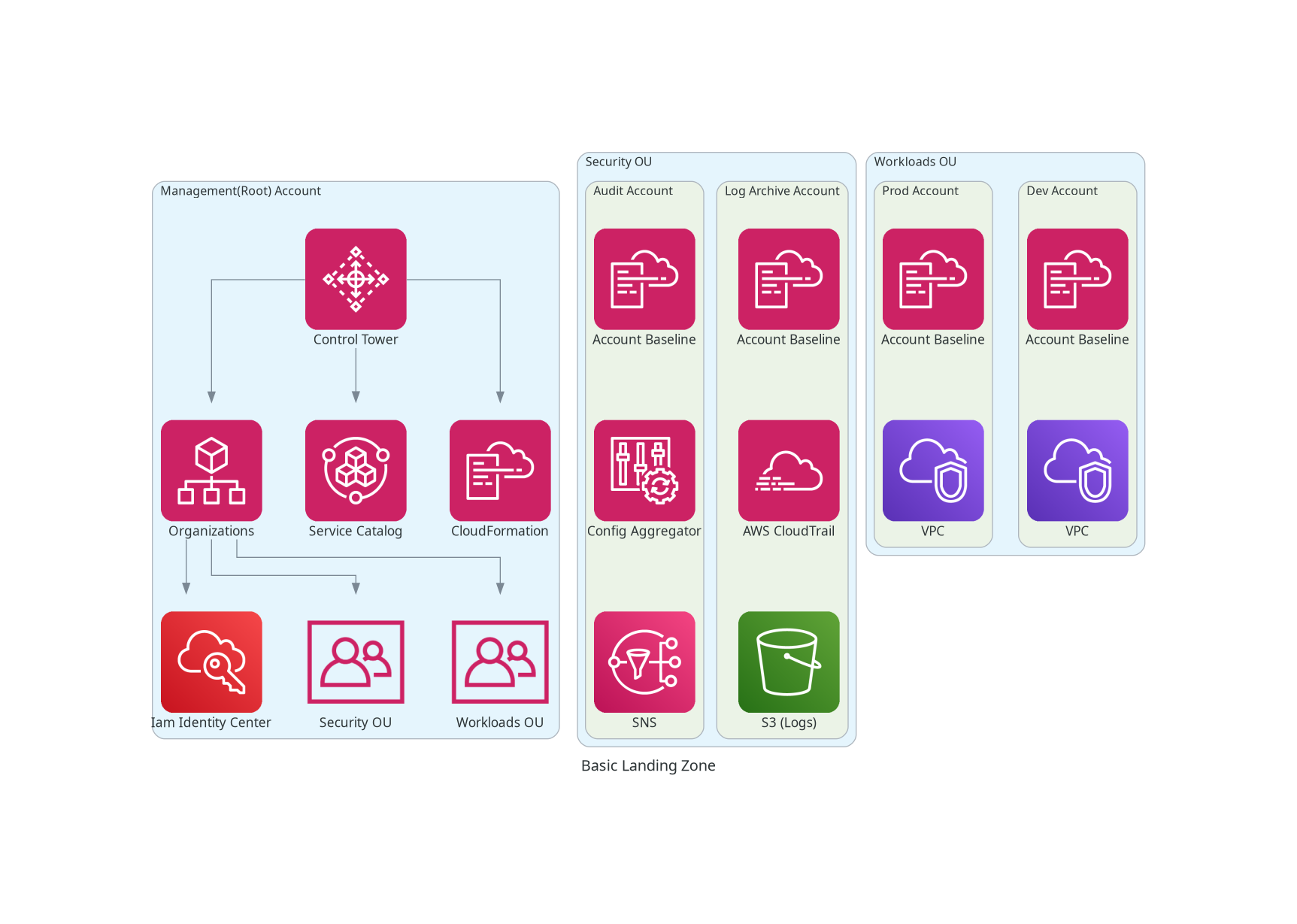
Accounts
- Management Account – The central account that oversees security, billing, and governance.
- Log Archive Account – Stores security and compliance logs to ensure accountability.
- Audit Account – Provides a restricted environment for security monitoring and compliance enforcement.
- Workloads accounts – Run workloads accounts such as Dev, Prod, etc
Key Services
- AWS Control Tower – Automates setup, governance, and best practices.
- AWS Organizations – Manages multiple accounts under a unified structure.
- AWS IAM Identity Center – Centralises user access management.
- AWS Identity and Access Management – Manages user permissions and access to AWS resources securely through policies, roles, and authentication mechanisms.
- AWS CloudTrail – Logs all API activity for security auditing.
- AWS CloudWatch – Monitors AWS resources and applications in real-time with logs, metrics, and alerts.
- AWS Config – Continuously tracks resource configurations for compliance over time.
- AWS Service Catalog – Manages approved AWS services for controlled self-service provisioning.
- AWS CloudFormation – Automates infrastructure creation and deployment using templates.
- Amazon Simple Storage Service (S3) – Provides scalable object storage.
- Amazon Simple Notification Service (SNS) – Enables push notifications and messaging across AWS services and external systems.
- AWS Lambda – Runs event-driven, serverless functions.
- AWS Step Functions – Orchestrates workflows by automating multi-step processes across AWS services.
Hybrid Cloud Landing Zone
A more elaborate landing zone could also be created, perhaps geared towards a generally larger-scale environment, or one focused on a certain domain or solution set. As a small example, a hybrid cloud landing zone would extend the basic landing zone by including additional network-related elements.
This landing zone extends the capabilities of the basic landing zone by incorporating network connectivity, security, and identity federation between cloud and on-prem environments.
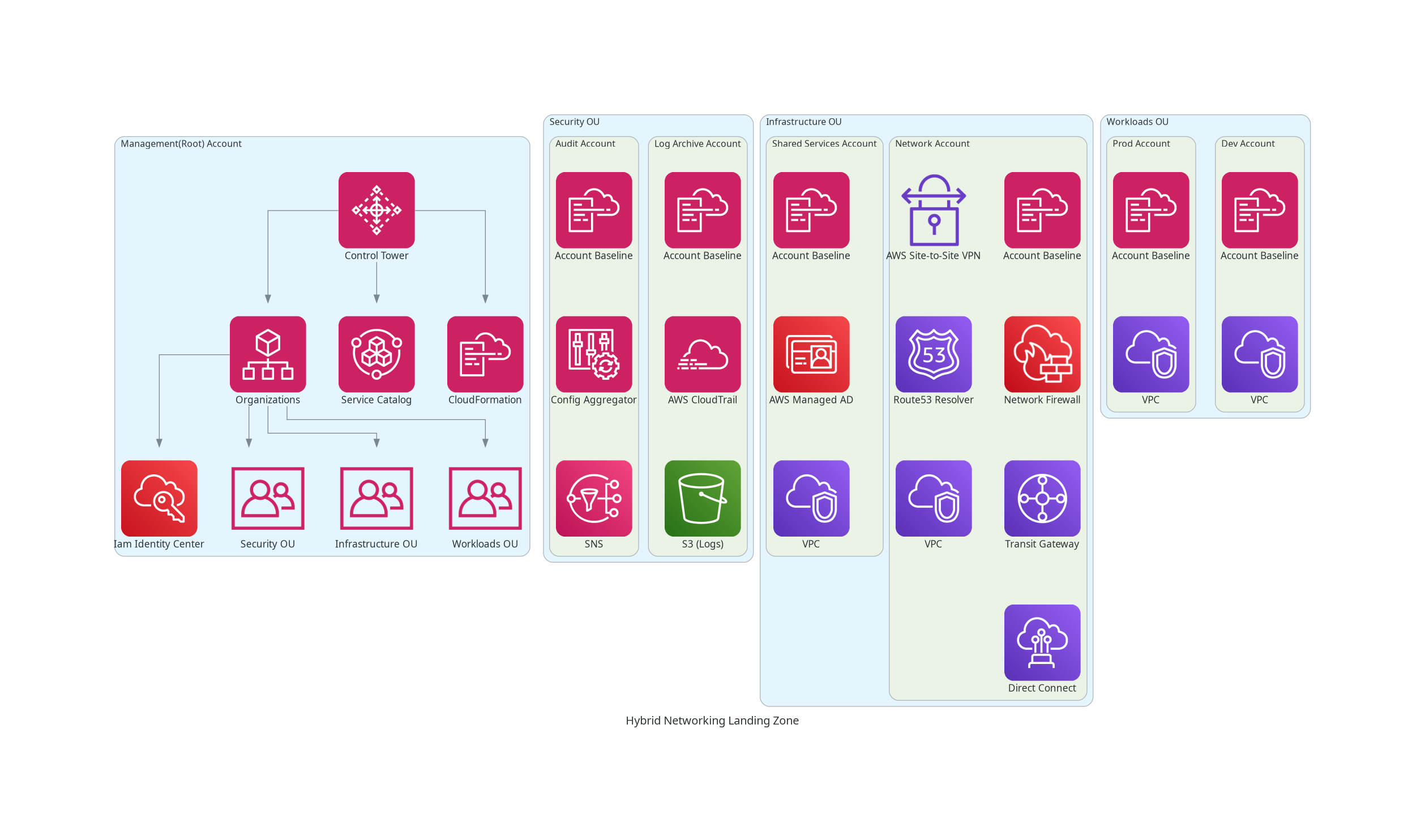
Accounts:
- All accounts from the Basic Landing Zone
- Networking Account – Manages hybrid connectivity with on-premises data centres.
- Shared Services Account – Hosts core services like Active Directory and monitoring.
Key Services:
- All services from the Basic Landing Zone
- AWS Transit Gateway – Enables centralised network routing to and among a large number of VPCs, across AWS accounts.
- AWS Direct Connect – Provides a dedicated, high-speed connection from on-premises sites to AWS.
- AWS Site-to-Site VPN – An encrypted VPN tunnel for secure communication between AWS and on-premises.
- AWS Managed AD – Extends on-prem Active Directory to AWS.
- Amazon VPC – A logically isolated network for AWS resources.
- AWS Route 53 – Provides domain name resolution between AWS and on-prem environments.
Leave a Reply